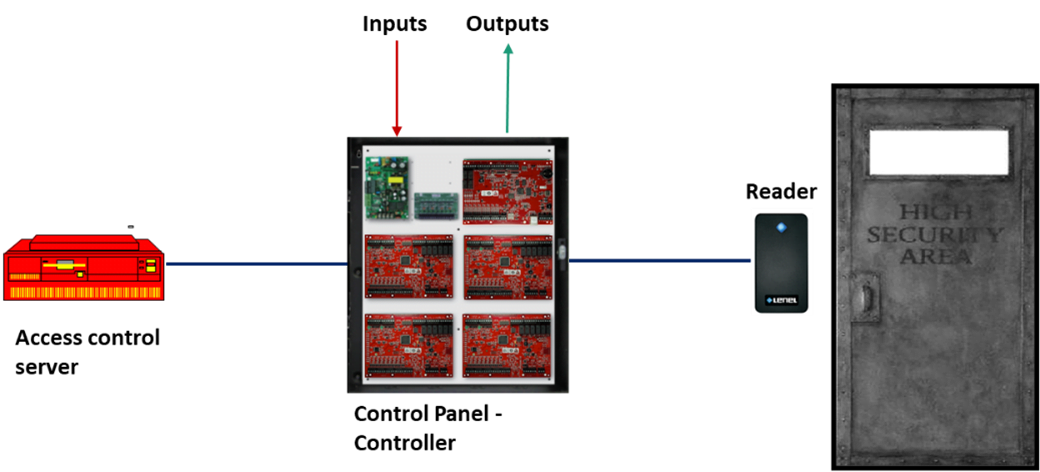
In short, a credential hold the user’s data (user identity) which is „read” by the reader, and sent it further to a „control panel -controller”, an intelligent device provided with a database. If the identity is found in the controller database, access is granted.
Six main types of credentials are used today, which offer different levels of security and convenience.
- PIN codes: Personal Identification Number. It is the most simple and cost-effective credential but requires users to remember the code (Personal Identification Number – PIN) when needed. PIN also provides pretty low security, and also is a slow authentication method, not useful in high-traffic areas.
- RFID low-frequency cards –„Prox cards”: Users present RFID-enabled cards in proximity to a reader and the encoded ID on the card is quickly read. They were widely used at the beginning of the 2000s, but due to their security vulnerabilities (the code is not encrypted) are not used anymore, but only with old or cheap systems.
- Smart cards : Advanced plastic cards with a computer chip embedded that can store, besides the ID code, additional information, like biometrics, but not only. They are more secure than Prox cards, as the data within the card is encrypted, and can only be accessed with proper „reading keys”. Probably the most popular technology today.
- Mobile solutions: the ultimate technology today. Users, after simply installing an app to their smartphone, can unlock the door, by just scanning the smartphone at the reader, or using an unlock feature in the app to gain access. Mobile credentials are more secure, cost-effective, and more convenient, being easily managed and used by normal employees, visitors, contractors, or service staff.
- Biometric solutions: Used more as an additional layer of security, biometric solutions overcome the problems of lost or stolen cards, as the person becomes the „key”, which is, obviously, more difficult to copy. The most widely used biometric technologies include fingerprint, facial recognition, and eye scanning for retinas or irises.
The most „well-known” component of an access control system, the reader is usually installed, on the wall, next to the door, outside, and sometimes also inside the protected area.
As its name says, the reader reads the compatible credential types. It does not take any access decision, just transfers the data from the card to the control panel which is the „decision maker”.
There are several types of security readers in use today such as:
- „Standard” Card reader: Usually of RFID technology, it detects credentials when they are within its magnetic field range, and reads the code written on the chip of the card. The more modern” standard” card readers use NFC and/or Bluetooth/Bluetooth Low Energy ( BLE) technology to read the new mobile virtual credentials from the user’s smartphone. The user needs to bring his smartphone close to the reader which reads the credential from the phone.
Some BLE (Bluetooth Low Energy) readers only request the user to wave his hand in front of the reader, just to communicate to the system the intention of passing through that door. The reader reacts and the ID is automatically read from the user’s smartphone, even if the phone is a pocket or purse. This is called touchless technology
Standard readers are suitable for heavy traffic areas.
- Keypad readers: allow users to type their unique PINs on a keypad installed on the wall, next to the door. However, PINs can be shared, willingly or not, guessed, or used by intruders, especially when keypad buttons wear over time. Because of these security issues, they are not often used alone, but only in certain situations.
- Card readers with Keypad: Users present their cards to the reader and once the system reads their card ID, they are asked to „identify themselves”, by typing their unique personal code, PIN. It’s called two-factor authentication. This reader type, more expensive than a standard one, is rather used in higher security areas, being less suitable for heavy traffic zones (the authentication procedure is slower).
- Biometric readers: This technology, theoretically eliminates the use of all „standard” credentials. The person becomes „the credential”, as the system relies upon approved biometric attributes ( fingerprints, face, iris, retina) for validation against a biometric database.
Thanks to continued advancements in artificial intelligence technology and faster processing speeds, biometric solutions remain at the forefront of high-end access control solutions. However, the prohibitive prices and GDPR concerns, prevent many companies to adopt this technology on a large scale.
- Video door readers: Video door readers have a TV camera built-in, giving security teams visual evidence of identity and any security issues. Practically, the TV reader camera replaces an extra TV camera, usually installed next to the controlled door, while it offers a better field of view.
- Intercom readers: This type of access control device integrates a video reader, with two-way audio, and is very helpful in verifying visitors prior to granting entry.
The Control Panel, or Controller is the „brain” of any access control system, and therefore it is the fundamental piece of hardware in the system ( and the most expensive hardware component).
This is a self-contained intelligent device, with its local processing power and sufficient capacity to store a full database of cardholders and other information required. Actually, it is a specialized computer, installed in the field, between the host computer and card readers.
The controller itself makes all of the decisions as to granting or denying access to a person, taking the processing load off the server access control app, and allowing the entire system to operate faster. This approach is called „distributed processing network architecture” (in contrast to a centralized architecture where decisions are taken by the host computer).
Due to this distributed structure, the access control system will continue to operate (lock and unlock doors) even if the communication line back to the host computer is interrupted, or the host computer is down.
An advanced powerful controller can support up to 64 doors (readers) but typically controller support between 2 and 16 doors. Bigger systems need more controllers.
Most of the controllers can be also, optionally, provided with digital inputs/outputs interfaces, which allows also for the connection of various devices like switches, buttons, motion detectors, etc, or sounders, beacons, small relays, and most anything that can be powered from a small DC voltage.
Almost all modern controllers are now directly connected to a company’s computer network, either through cable or wireless. Newer systems are taking the network connection all the way down to the reader interface or even the reader at the door ( lower wiring costs).
The Access control application has three main functions: to monitor, to configure and to manage the access, alarms and outputs in the security system. It is the glue that holds a complex system together and makes it work.
The software for access control systems is a vital tool for managing the database of authorized users. The database holds the details of the network of access-controlled doors and authorized users together with their access levels. To maintain security, it’s essential to keep the database up-to-date by adding new users and removing users who have left or who no longer have permission to access specific areas.
There are two options for hosting access control software:
- on-site in servers (when the systems are called “on-premise”)
- hosted in the cloud accessible via the Internet, where the access control app is installed in a cloud and there is no hardware and software on-site anymore.
1 On-Premise systems
Small „on-premise” access control systems usually have the access control application installed on a simple desktop/laptop computer, which is used as the host computer, but often is also used as a client workstation for entering cardholder information, programming the system, and making status reports.
In larger systems, as access control devices can produce high volumes of data, there is needed one or more dedicated servers, which are high-speed computers able to perform several thousand operations per second: essential for controlling the flow of data back and forth across the system. Mission Critical systems usually use a secondary server that is kept on standby to act as a redundancy for the primary server should it fail or need periodic maintenance.
As the servers are quite expensive, there are systems that allow installation on company’ virtual machines.
2 Cloud-based systems
What are cloud access control systems? While the field hardware ( controllers, readers, etc) will be still on-site, the software (database, logic) is hosted in the cloud, so there is no need for local servers, clients operating systems, databases, etc.
Cloud-based systems offer the same basic functionalities of on-premise software, and even more, without the operators or system administrators necessarily needing to be in that physical workspace to utilize the system, so they are no longer restricted to reviewing data onsite but from any location using an Internet-connected fixed or mobile device.
Also, cloud-based systems are more scalable and reliable; additional capacity is available on demand for a higher subscription, and the maintenance and updates are usually handled by the hosting company as part of the subscription.
For more information click here.